SSL Certificate Check
Example
The full source code for this example is available here
Managing SSL certificate expiration dates manually can be a challenging and error-prone task, especially in environments with a large number of hostnames to check.
Failing to renew certificates on time can result in unexpected outages and security breaches. To address this issue, you can use Plombery to automate the monitoring of SSL certificate expiration dates and receive notifications when a certificate is due to expire.
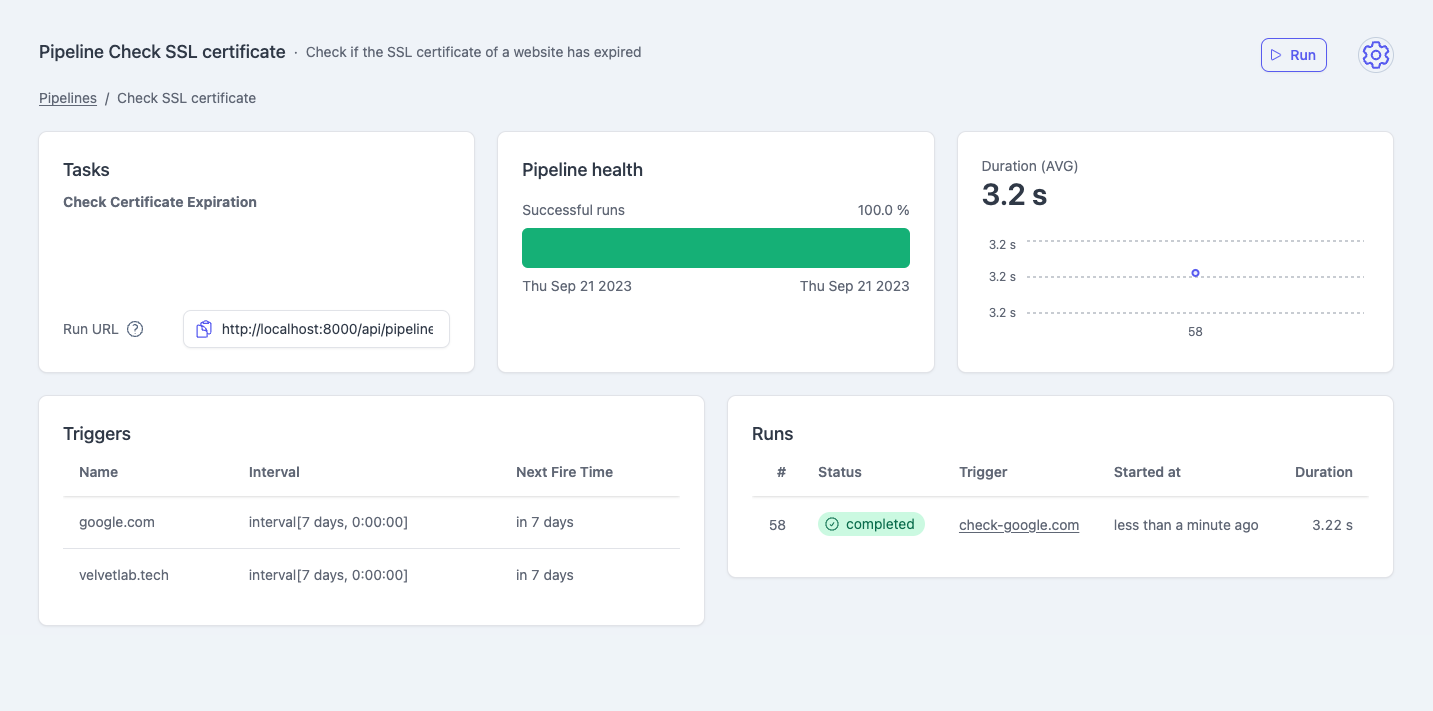
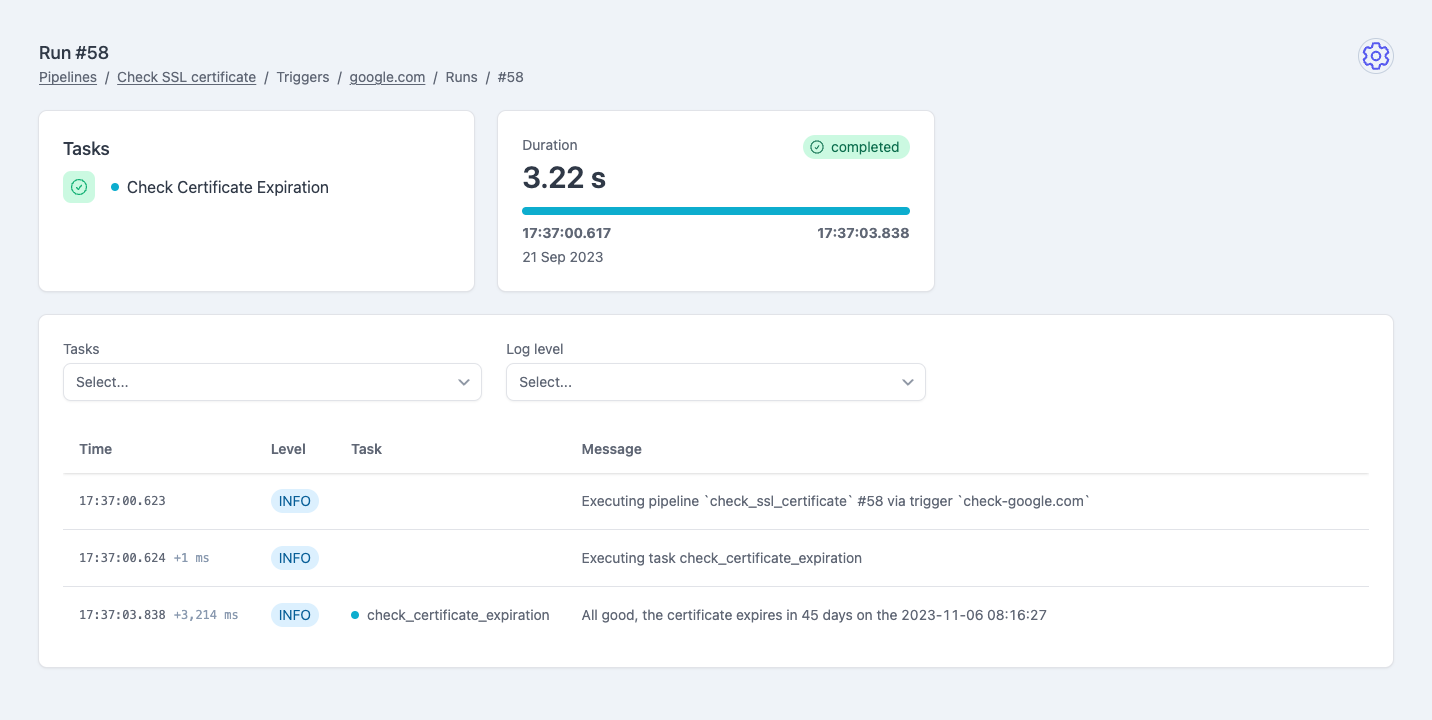
You can also run an SSL check on the fly via the manual trigger:
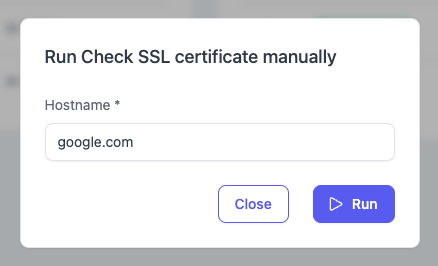
How to
Define a list of hostnames you want to check and create 1 trigger for each of them so once a trigger fails you know which hostname is concerned:
hostnames = [
"google.com",
"velvetlab.tech",
]
register_pipeline(
id="check_ssl_certificate",
name="Check SSL certificate",
description="""Check if the SSL certificate of a website has expired""",
tasks=[check_certificate_expiration],
triggers=[
# Create 1 trigger per each host to check
Trigger(
id=f"check-{host}",
name=host,
description="Run the pipeline every week",
params=InputParams(hostname=host),
schedule=IntervalTrigger(
weeks=1,
),
)
for host in hostnames
],
params=InputParams,
)
The pipeline in this example has only 1 task but you could add additional checks on the SSL certificate as additional tasks:
@task
async def check_certificate_expiration(params: InputParams):
logger = get_logger()
now = datetime.utcnow()
info = get_certificate_info(params.hostname)
expiration: datetime = info.get("notAfter")
if expiration <= now:
raise Exception(f"The certificate expired on {expiration}")
expires_in = expiration - now
if expires_in.days < EXPIRATION_WARNING_THRESHOLD:
raise Exception(f"Attention, the certificate expires in {expires_in.days} days")
logger.info(
f"All good, the certificate expires in {expires_in.days} days on the {expiration}"
)